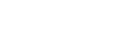In a scenario where cyber attacks are becoming increasingly sophisticated, Brazil is taking a decisive step towards transforming its defensive posture into a collective intelligence strategy. With the publication of GSI/PR Ordinance No. 148 of 2025, the country formalizes the creation of ISACs in Brazil, a model that strengthens cyber intelligence - structures inspired by international models already consolidated in the world's largest economies.

The initiative puts Brazil in line with the most advanced cybersecurity strategies globally. The United States, Canada, Japan, the European Union, Singapore and India have been operating sectoral ISACs for years, as documented by the National Council of ISACs, promoting the exchange of threat information and coordinating response actions that benefit entire ecosystems.
In Brazil, the centers will bring together representatives from the public and private sectors in strategic segments - such as energy, finance, telecommunications, transport and health - with the aim of sharing information about threats in real time, especially at a time when coordinated attacks against critical infrastructures are intensifying.
The Power of Distributed Intelligence in Cybersecurity
The logic behind ISACs is straightforward: distributed intelligence to contain exponential risks. A clear example would be a ransomware attack against a logistics operator. Instead of reacting in isolation, the company communicates the incident to the sectoral ISAC, which redistributes the data, allowing other organizations to react proactively. What was once a localized incident becomes a preventive alert for the entire chain.
International experience shows that sectors that have implemented mature ISACs have managed to significantly reduce the average time taken to detect and respond to threats. In the American financial sector, FS-ISAC has enabled financial institutions to identify phishing campaigns earlier, as documented by the Cyber Security Summit Brazil.
More than an alert channel, ISACs function as strategic intelligence centers, where organizations collectively build knowledge and response capacity, especially relevant in a country with continental dimensions like Brazil.
Benefits of ISACs in Brazil for organizations
The implementation of ISACs in Brazil brings tangible benefits to the participating organizations:
Access to qualified intelligence: The FS-ISAC in the US provides threat alerts specific to the financial sector on a regular basis. This early intelligence approach is similar to that offered by Asper's Cyber Fusion Center , which operates with predictive intelligence to anticipate threats.
Reducing response times: Organizations participating in ISACs are able to significantly improve their detection and response times, according to a Cisco report. During global security events, such as the WannaCry attack, members of sector ISACs implemented protection measures faster than the market average. In addition, the use of incident response orchestration systems (SOAR) integrated with ISACs has proven to be an effective practice in mature centers, as demonstrated in publications by MITRE and ENISA. Such integrations significantly reduce incident containment and remediation time.
Resource savings: Studies by the Ponemon Institute indicate that organizations participating in ISACs are able to optimize their security investments by avoiding duplication of analysis efforts and taking advantage of the sector's collective intelligence.
Expanded view of threats: E-ISAC gives its members access to a knowledge base on specific threats to the electricity sector that is significantly larger than individual organizations could build. This expanded visibility is crucial for identifying targeted campaigns in specific sectors.
Regulatory alignment: Organizations participating in ISACs demonstrate greater compliance with regulatory requirements related to cyber security, according to the Financial Services Roundtable. Regulators such as the Central Bank of Brazil have already signaled that participation in ISACs will be considered a positive indicator in maturity assessments.
ISACs as a Market Strategy and Competitive Differential
The new ordinance stipulates that ISACs will be organized by economic sectors or technical domains. Interested companies must seek integration with the ISAC most compatible with their activity and commit to minimum standards of security, confidentiality and interoperability, according to GSI/PR Ordinance No. 148.
It's not just about security. It 's about market strategy. Getting closer to the government, anticipating regulatory requirements and having access to qualified intelligence can represent a clear competitive advantage, especially in sectors with strong compliance pressure. In a market where trust is increasingly becoming a competitive differentiator, actively participating in ISACs signals a commitment to the security of the ecosystem as a whole.
Organizations that adopt a proactive stance in this movement will be positioning themselves as leaders in digital maturity and corporate responsibility. In a scenario where security incidents frequently make the headlines, demonstrating commitment to collaborative practices can be a significant differentiator in building the trust of customers and partners.
The Role of Threat Intelligence in the Age of ISACs
The effectiveness of ISACs is directly linked to the quality of the threat intelligence shared between the participants. In this context, robust threat intelligence solutions are essential for:
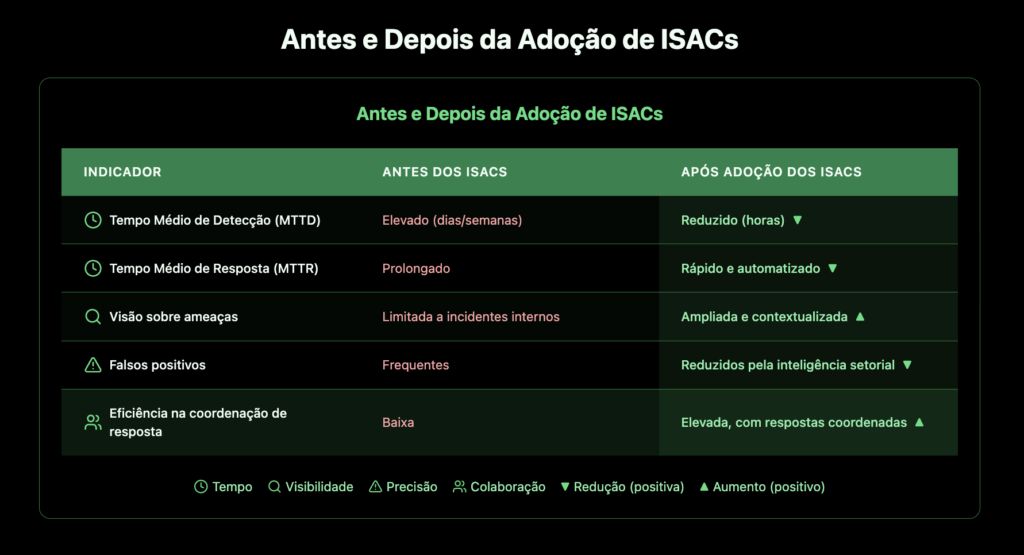
Data collection and processing: The FS-ISAC processes a large volume of commitment indicators shared by its members on a daily basis. This proactive approach is paralleled by Asper's Cyber Fusion Center, which uses big data technologies to transform indicators into actionable intelligence.
ISACs operate according to the Threat Intelligence lifecycle: collection, processing, analysis, dissemination and feedback, a practice recommended by frameworks such as the MITRE ATT&CK and ENISA frameworks.
Threat contextualization: Health-ISAC has documented how sector contextualization of security alerts significantly reduces false positives in hospital environments. Asper's Cyber Fusion Center already operates with this philosophy, applying sector context to alerts.
Response automation: E-ISAC has demonstrated how companies in the electricity sector that implement automation based on shared intelligence are able to improve their threat containment times. This capability is enhanced in Asper's Cyber Fusion Center, where orchestration allows countermeasures to be implemented in multiple systems simultaneously.
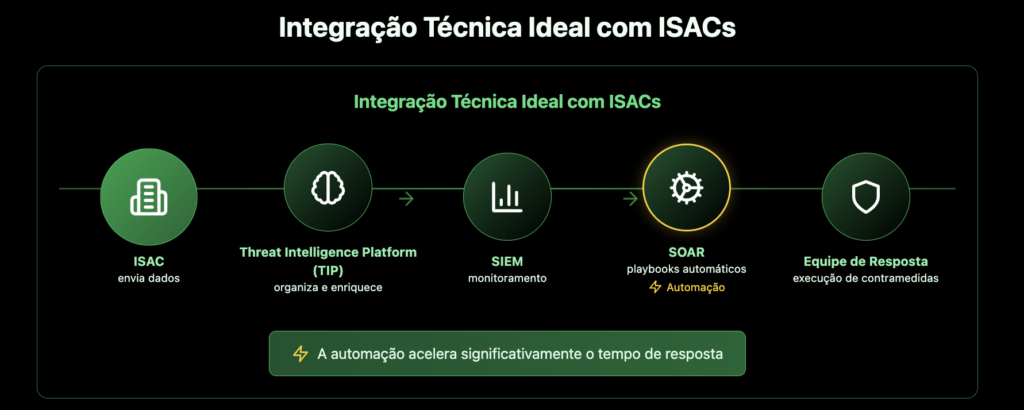
Organizations with SIEM + SOAR integration + STIX/TAXII feeds are able to automate IoC-based detections from ISACs, reducing Mean Time to Respond (MTTR) and Mean Time to Detect (MTTD), boosting the defense capacity of participating organizations.
Correlation of events: During coordinated attacks against specific sectors, ISACs have been able to identify patterns that connect seemingly isolated incidents in different organizations. This holistic view is one of the hallmarks of the Cyber Fusion Center model, which has evolved beyond the traditional SOC.
Effectiveness metrics: Automotive ISAC has implemented metrics frameworks that demonstrate significant improvements in remediation time for critical vulnerabilities among participating manufacturers. Mature operations, such as those found in Cyber Fusion Centers, use real-time dashboards to demonstrate the value of shared intelligence.
Just as ISACs increase inter-organizational collaboration, their effectiveness is directly related to the adoption of recognized good technical practices, such as:
- Integration with Cyber Threat Intelligence (CTI) platforms.
- Segmentation of critical sectors for better targeting of intelligence.
- Alignment with frameworks such as NIST SP 800-150, ISO 27035 and MITRE ATT&CK.
Challenges in Implementing ISACs in Brazil
Despite the obvious benefits, the successful implementation of ISACs in Brazil will face significant challenges:
- Culture of secrecy: A Cisco survey revealed that many Brazilian organizations are still reluctant to share information about incidents, fearing reputational impacts. This cultural barrier will need to be overcome if ISACs are to succeed in Brazil.
- Asymmetry of maturity: The Igarapé Institute report documented significant differences in the levels of investment in security between Brazilian companies. This disparity can create imbalances in the quality of contributions to ISACs.
- Financial sustainability: A GSI study estimated that the full operation of a sectoral ISAC in Brazil would require significant annual investments. The mixed financing model (public-private) has proven effective internationally, but there is still no clarity about the Brazilian model.
- Technical standardization: A pilot sharing project between Brazilian banks faced difficulties due to incompatible formats. The adoption of standards such as STIX/TAXII will be crucial for the success of the Brazilian initiative and to guarantee interoperability between different sectors.
International experience shows that successful ISACs generally start with a limited scope and gradually expand their activities as trust and perceived value increase.
How to Prepare Your Organization for the ISAC Era
To make the most of the benefits of ISACs, organizations need to:
- Assess your current maturity: A Gartner study revealed that many organizations overestimate their ability to consume and apply external threat intelligence. A structured assessment can help identify specific gaps in intelligence processing capacity.
- Establish internal processes: Organizations that implement formal processes for intelligence management before joining ISACs obtain greater value from participation, according to the Ponemon Institute. The creation of teams dedicated to the analysis and application of external intelligence can significantly increase the implementation of effective countermeasures.
- Training teams: According to ISACA, only a fraction of security professionals in Brazil have formal training in threat intelligence analysis. This continuous development approach is similar to that adopted at Asper's Cyber Fusion Center, where analysts receive specialized training.
- Implement enabling technologies: A Gartner study showed that organizations with dedicated Threat Intelligence Management platforms are able to operationalize more threat indicators. Implementing APIs for automated ingestion of ISAC feeds multiplies the value of shared intelligence.
- Developing a culture of sharing: A program in the Brazilian banking sector documented that organizations with clear policies on what can be shared contribute more effectively to the collective intelligence ecosystem. Leaders who regularly communicate the value of sharing help establish a collaborative culture.
Preparation for effective participation in ISACs must begin well before formal membership, with internal practices that facilitate future integration.
Recommended Technical Practices for Integrating ISACs Effectively
To maximize the benefits of participating in an ISAC, organizations should adopt the following technical practices:
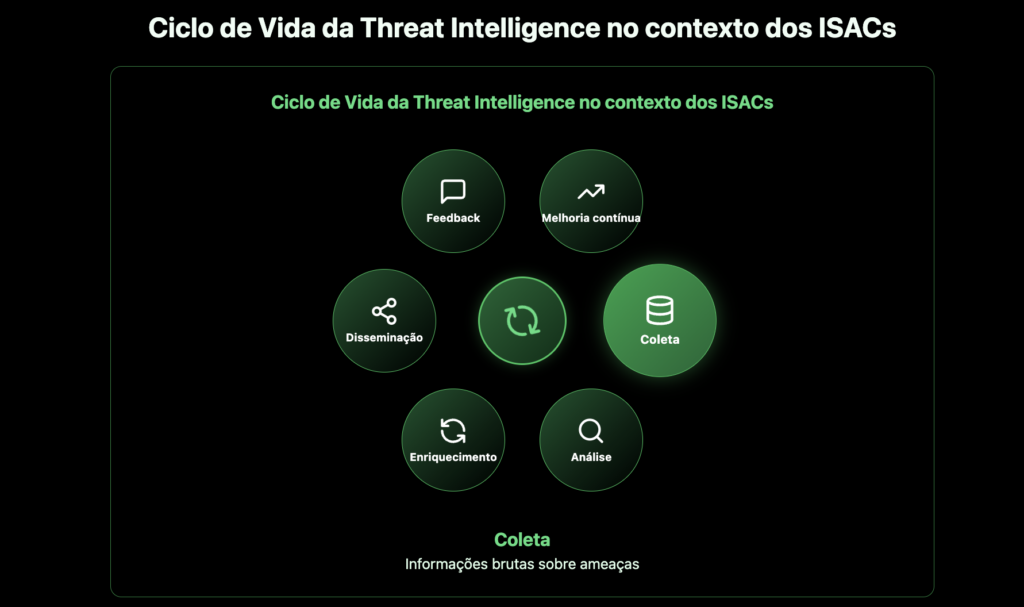
- Implement STIX/TAXII standards: These are the most widely used open formats for structured sharing of Indicators of Commitment (IoCs) and Tactics, Techniques and Procedures (TTPs), ensuring interoperability between systems and partners.
- Use Threat Intelligence Platforms (TIP): Tools such as MISP (Malware Information Sharing Platform) make it possible to organize, enrich and distribute the intelligence received from ISACs, facilitating automation and internal sharing.
- Integrate with automation and response tools (SOAR): The adoption of automatic playbooks, such as those available in Cortex XSOAR or Splunk SOAR, makes it possible to react quickly to critical IoCs distributed by ISACs.
- Create an internal incident sharing policy: Establish clear guidelines on what information can or should be shared, including levels of anonymization, and define those responsible for approval, such as the CISO or DPO.
- Test and validate indicators: Before acting on incoming IoCs, organizations must check their validity and relevance with appropriate tools, ensuring the effectiveness of response actions.
- Carry out simulations based on shared scenarios: For example, train teams to respond to simulated phishing campaigns that reflect real threats reported to ISAC.
The Future of Security is Collaborative
The adoption of ISACs in Brazil represents more than a technical change, it is a cultural transformation in the way we approach cyber security. By migrating from an isolated model to a collaborative approach, the country is taking a significant step towards a more resilient digital ecosystem that is prepared to face increasingly sophisticated threats.
This collaborative evolution is paralleled by the transformation of traditional security operations centers to more advanced models, such as Asper's Cyber Fusion Centers, which integrate multiple security disciplines and intelligence sources. Just as ISACs represent an evolution in inter-organizational collaboration, Cyber Fusion Centers mark a transformation in intra-organizational collaboration, creating an ecosystem where intelligence flows freely and is transformed into preventive action.
Organizations that understand the strategic value of this change and proactively position themselves in this movement will not only be strengthening their individual defenses, but will be contributing to raising the digital maturity of the country as a whole. In a world where cyber attacks ignore organizational and geographical boundaries, shared intelligence becomes not only a competitive advantage, but a strategic necessity.
The Brazilian ISACs arrive as a platform to materialize this vision and transform the way we protect our most valuable digital assets. The time to start preparing is now, even before the first sectoral ISACs are fully operational in the country.